Per desplegar el vagrant en les nostres màquines, hem utilitzat una configuració especial. Les màquines utilitzades són: windows server 2019, windows 10, ubuntu i rocky. També en totes les màquines hem utilitzat tres adaptadors: un en NAT per el vagrant, el internal network per la red interna de la màquina y una altre en bridge adapter per a la red de la classe (només en el router).
Aquesta és la configuració:
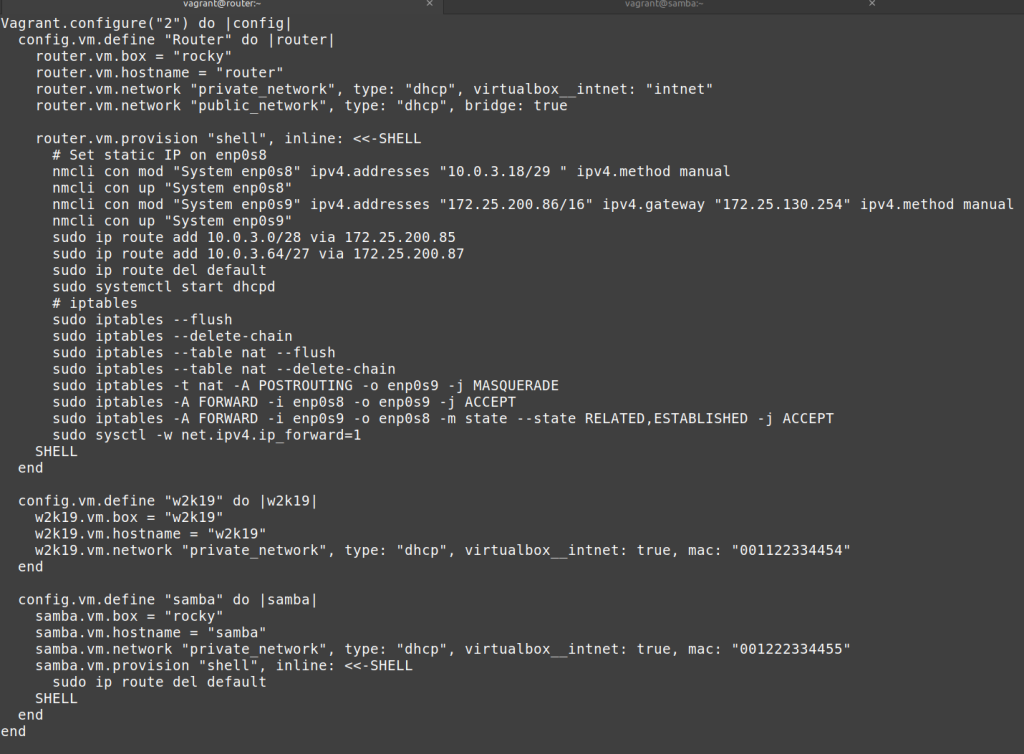
Vagrant.configure(“2”) do |config|
config.vm.define “Router” do |router|
router.vm.box = “rocky”
router.vm.hostname = “router”
router.vm.network “private_network”, type: “dhcp”, virtualbox__intnet: “intnet”
router.vm.network “public_network”, type: “dhcp”, bridge: true
router.vm.provision "shell", inline: <<-SHELL
# Set static IP on enp0s8
nmcli con mod "System enp0s8" ipv4.addresses "10.0.3.18/29 " ipv4.method manual
nmcli con up "System enp0s8"
nmcli con mod "System enp0s9" ipv4.addresses "172.25.200.86/16" ipv4.gateway "172.25.130.254" ipv4.method manual
nmcli con up "System enp0s9"
sudo ip route add 10.0.3.0/28 via 172.25.200.85
sudo ip route add 10.0.3.64/27 via 172.25.200.87
sudo ip route del default
sudo systemctl start dhcpd
# iptables
sudo iptables --flush
sudo iptables --delete-chain
sudo iptables --table nat --flush
sudo iptables --table nat --delete-chain
sudo iptables -t nat -A POSTROUTING -o enp0s9 -j MASQUERADE
sudo iptables -A FORWARD -i enp0s8 -o enp0s9 -j ACCEPT
sudo iptables -A FORWARD -i enp0s9 -o enp0s8 -m state --state RELATED,ESTABLISHED -j ACCEPT
sudo sysctl -w net.ipv4.ip_forward=1
SHELLend
config.vm.define “w2k19” do |w2k19|
w2k19.vm.box = “w2k19”
w2k19.vm.hostname = “w2k19”
w2k19.vm.network “private_network”, type: “dhcp”, virtualbox__intnet: true, mac: “001122334454”
end
config.vm.define “samba” do |samba|
samba.vm.box = “rocky”
samba.vm.hostname = “samba”
samba.vm.network “private_network”, type: “dhcp”, virtualbox__intnet: true, mac: “001222334455”
samba.vm.provision “shell”, inline: <<-SHELL
sudo ip route del default
SHELL
end
end
Comandes per vagrant:
vagrant up ————- Per iniciar la màquina
vagrant ssh ———— Per entrar dins de la màquina, només en distribucions linux
vagrant halt ———— Per tancar la màquina
vagrant destroy ——- Per eliminar la màquina
Aquí està el vagrantfile dels clients:
Vagrant.configure(“2”) do |config|
# Ubuntu
config.vm.define “client3” do |ubuntu|
ubuntu.vm.box = “ubuntu”
ubuntu.vm.hostname = “ubuntu”
ubuntu.vm.communicator = “ssh”
# Red de adaptador interno y adaptador puente
ubuntu.vm.network "private_network", type: "dhcp", virtualbox__intnet: true
#ubuntu.vm.provider "virtualbox" do |vb|
# vb.name = "Ubuntu_VM"
# vb.cpus = 2
# vb.memory = 2048
# vb.gui = false # Sin GUI
#endend
config.vm.define “Router3” do |router|
router.vm.box = “rocky”
router.vm.hostname = “router”
router.vm.network “private_network”, type: “dhcp”, virtualbox__intnet: “intnet”
router.vm.network “public_network”, type: “dhcp”, bridge: true
router.vm.provision "shell", inline: <<-SHELL
# Set static IP on enp0s8
nmcli con mod "System enp0s8" ipv4.addresses "10.0.3.65/27" ipv4.method manual
nmcli con up "System enp0s8"
nmcli con mod "System enp0s9" ipv4.addresses "172.25.200.87/16" ipv4.gateway "172.25.130.254" ipv4.method manual
nmcli con up "System enp0s9"
sudo ip route add 10.0.3.16/29 via 172.25.200.86
sudo ip route add 10.0.3.0/28 via 172.25.200.85
sudo ip route del default
# iptables
sudo iptables --flush
sudo iptables --delete-chain
sudo iptables --table nat --flush
sudo iptables --table nat --delete-chain
sudo iptables -t nat -A POSTROUTING -o enp0s9 -j MASQUERADE
sudo iptables -A FORWARD -i enp0s8 -o enp0s9 -j ACCEPT
sudo iptables -A FORWARD -i enp0s9 -o enp0s8 -m state --state RELATED,ESTABLISHED -j ACCEPT
sudo sysctl -w net.ipv4.ip_forward=1
SHELLend
config.vm.define “w10” do |w10|
w10.vm.box = “w10”
w10.vm.hostname = “w10”
w10.vm.network “private_network”, type: “dhcp”, virtualbox__intnet: true
end
end
